Research & Articles
Sharing what the data shows us.
When Headcount Doesn’t Help
The practical implication is a reframe of how programs are governed. Most teams measure remediation volume—tickets closed, patch compliance rates, mean time to remediate. These metrics describe throughput. They do not measure the marginal risk reduction of each remediation slot. Under constrained optimization, what matters is not how many findings you close but whether each slot is allocated to the vulnerability that reduces exploitability probability the most at the margin.
Say Goodbye to Kenna — Say Hello to Local Models at Scale
Last week, Cisco announced the End of Life of Cisco VM (Kenna Vulnerability Management), a company and product I spent the better part of 13 years building. Needless to say, this brought me through the whole range of emotions, but it also served as a great way to reflect on that time.
New Features: Critical Indicators & Known Exploitation Calendar Heatmap
We built critical indicators to explain the reasoning behind any CVE’s Empirical Score (0% - 100% real-world exploitation risk). Every CVE we analyze is modeled against over 2,000 data points. We took these model weight contributions and grouped them into the following categories: Chatter, Exploitation, Threat Intelligence, Vulnerability Attributes, Exploit Code, References, and Vendor.
Risk Model Slop
In cybersecurity risk scoring, “risk model slop” is the quiet but widening gap between what a probability means in a model and how vendors distort it once it leaves its original calibration.
Local Models vs Global Scores: Why Context Isn’t Enough
Context improves interpretation; local models improve decisions. If you want autonomous, defensible security actions, invest in a model that learns your environment and keeps learning as it changes.
Finding New Exploits with A Bespoke Model
“Why do we need another scoring system?” is not the best question to ask. Instead we need to get accustomed to asking about performance. This post walks through an example from our latest improvement to our exploit code classifier.
It’s Not About Making a Scoring System
“Why do we need another scoring system?” is not the best question to ask. Instead we need to get accustomed to asking about performance. This post walks through an example from our latest improvement to our exploit code classifier.
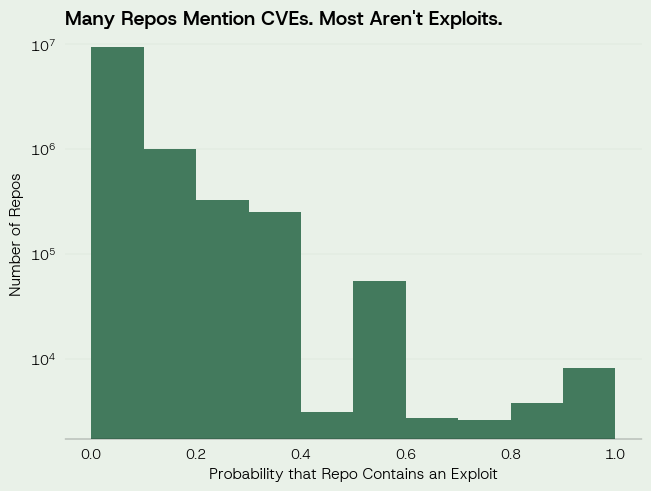
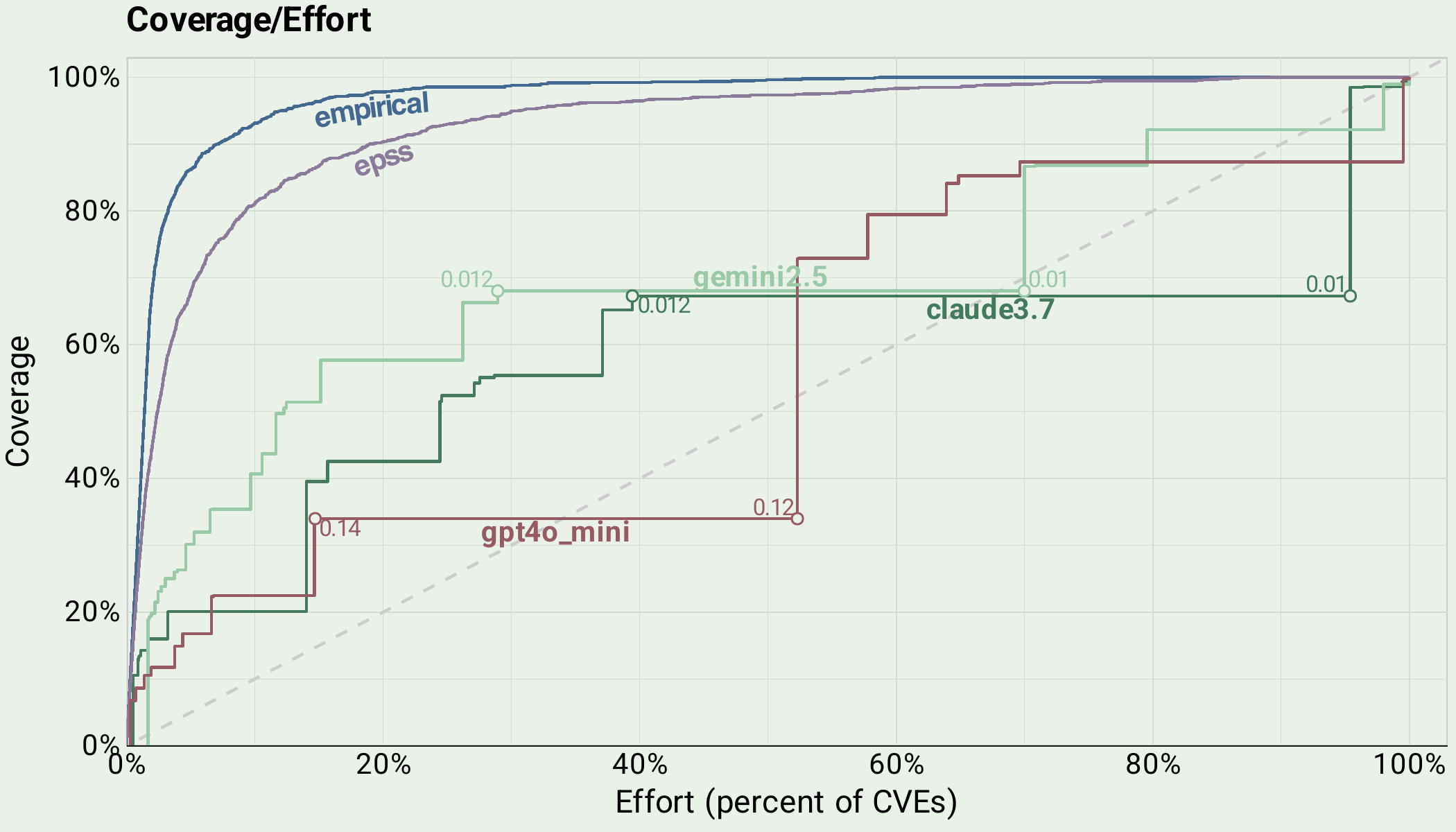
Benchmarking LLMs on the Vulnerability Prioritization Task
LLMs underperform EPSS in estimating vulnerability exploitation in the next 30 days.
Known Exploited vs Recently Exploited
Past exploitation is not a guarantee of future exploitation. However, recent exploitation is in fact a powerful predictor of future exploitation!